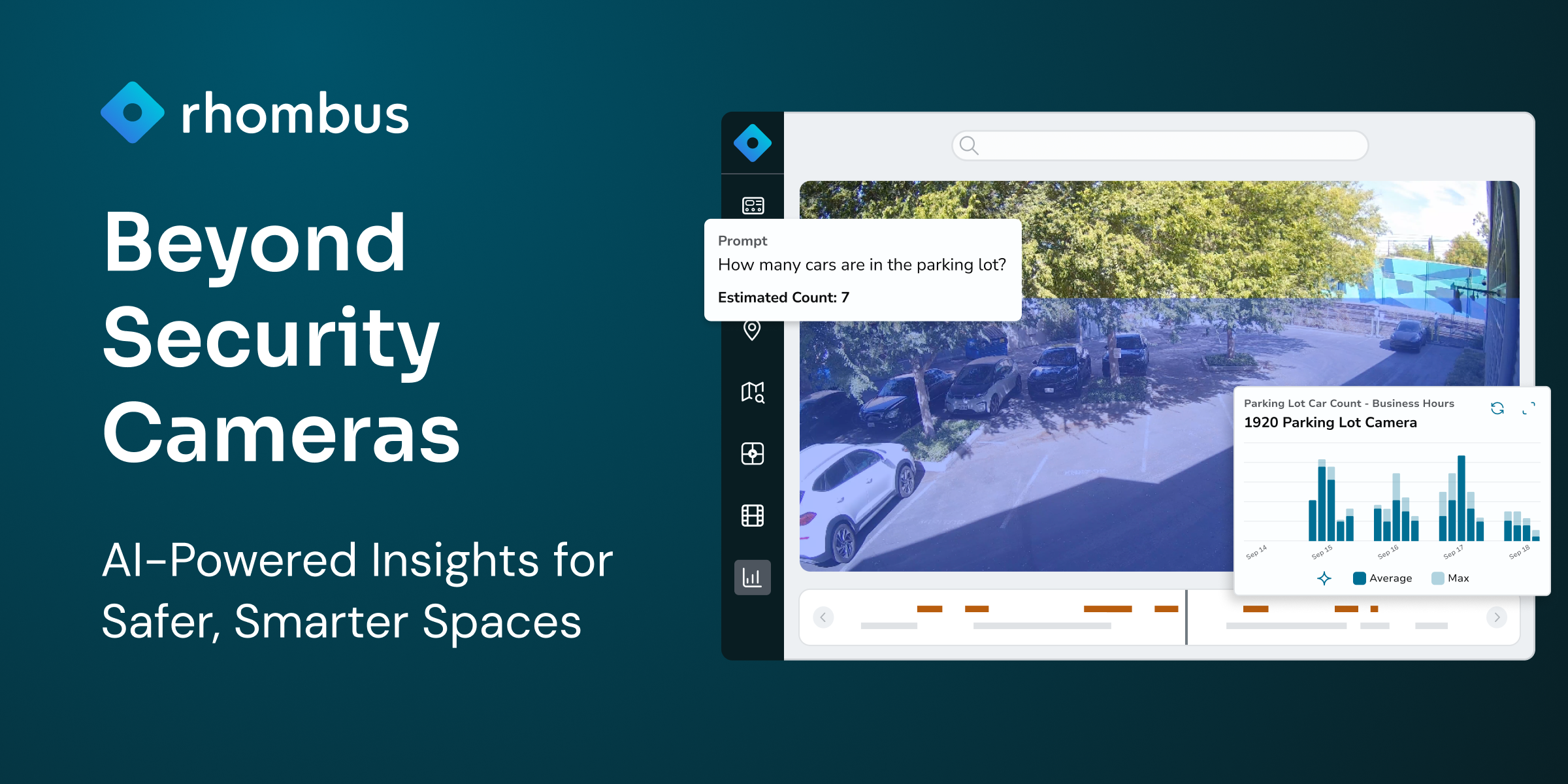
Physical Access Control Systems for Enhanced Security: A Comprehensive Guide

In today’s evolving security landscape, protecting physical spaces has become a critical priority for organizations of all sizes. Security breaches can have far-reaching consequences that affect operations, employee confidence, and customer trust. Physical Access Control Systems (PACS) serve as the first line of defense for organizations by effectively regulating who can enter specific areas within a facility. This makes access control important for minimizing security risks and significantly reduces vulnerability to security threats.
This guide explores everything you need to know about physical access control systems—from core components and functionality to key considerations for choosing the right solution for your organization’s needs.
What is a Physical Access Control System?
A physical access control system is a comprehensive security solution designed to regulate and monitor entry to facilities, buildings, or specific areas within a property. These sophisticated systems replace traditional lock-and-key methods with advanced technology that provides greater control, visibility, and management of who can access different parts of your premises.
At its core, a physical access control system authenticates identities through access control credentials like key cards, mobile phones, or biometrics, authorizes or denies access based on permissions, creates audit trails of activities, integrates with other security systems, and centralizes management across locations.
Modern access control systems have evolved beyond simple door security to become intelligent, networked platforms that support broader security objectives and operational efficiencies.
Why are Physical Access Control Systems Critical for Security?
Centralized Access Control Management
Physical access control systems provide organizations with centralized oversight of their entire security framework. An access control list (ACL) is essential in modern access control challenges, especially in distributed IT environments, to assign proper authorization and automate permission management. This comprehensive visibility allows security teams to monitor entry points in real-time, apply consistent security policies across locations, quickly modify access permissions as needed, identify potential vulnerabilities, and respond rapidly to security incidents.
Regulatory Compliance and Risk Mitigation
Many industries face strict regulatory requirements regarding physical security and data protection. Access control systems help organizations meet industry-specific compliance standards, demonstrate due diligence through detailed access logs, protect sensitive areas containing confidential information, reduce liability through documented security protocols, and maintain evidence for audits and investigations.
Additionally, access management systems play a crucial role in implementing robust access control policies and ensuring authorized use of resources, thereby minimizing security risks associated with unauthorized access.
Business Continuity and Operational Efficiency
Beyond security benefits, modern access control systems contribute to smoother business operations by eliminating the disruption of rekeying locks, automating access schedules, reducing administrative overhead through self-service access requests, preventing unauthorized access that could disrupt critical operations, and providing peace of mind to employees.
Key Components of Physical Access Control Systems
Access control readers are a crucial component of physical access control systems, comprising several interconnected elements that work together to create a comprehensive security solution:
Access Points and Authentication Methods
The front-end components include electronic locks and door controllers that secure physical entry points, and credential readers that validate access permissions through various methods like card readers, biometric scanners, PIN pads, mobile credential readers, or multi-factor authentication combining multiple methods. Mobile access control empowers users to gain access to secured spaces using smartphones or wearable devices, offering enhanced security, cost reduction, and convenience.
Core Infrastructure and Management Systems
Behind the scenes, sophisticated infrastructure supports operations: access control panels connecting readers to the central system, credentials database storing user information, management software for administering access rules, event logging systems creating audit trails, and notification mechanisms for security events. System administrators play a crucial role in managing these systems, utilizing automated provisioning systems to configure user permissions according to established access control policies and job responsibilities.
Integration Components
Modern access control systems typically connect with video surveillance systems for visual verification, intrusion detection systems for perimeter security, time and attendance applications, visitor management systems, and building automation systems. Logic-based access control plays a crucial role in securing connections to computer networks, system files, and data. These integrations create a unified security ecosystem that maximizes effectiveness.
How Do Physical Access Control Systems Work?
When someone attempts to enter a secured area, a multi-step process involving access controls occurs almost instantaneously:
- The individual presents their access credential to the reader
- The system verifies the credential against authorized identities
- The system confirms whether the user has permission for the specific door, area, and time
- Based on authorization results, access is either granted or denied
- The system records the access attempt, including time, location, and outcome
- For denied access or security concerns, alerts may be triggered
This process happens in seconds, providing security without impeding legitimate movement, powered by sophisticated technology including access control software, communication networks, database management, encryption technologies, and backup systems.
Access Control Integrations with Security Platforms
Modern security requires a holistic approach where multiple systems work in concert to protect assets and people. When access control integrates with other security technologies, the combined capabilities create a security posture greater than the sum of its parts. It is crucial to find the best access control solution to enhance security across a range of facilities.
The Power of Integrated Security
Consider this common security scenario: An employee approaches a restricted area after hours. When they present their credential:
- The access control system checks permissions and notes the unusual time
- Integrated surveillance cameras automatically focus on the entry point
- The system grants access if authorized but flags the event for review
- Security personnel receive a notification with live video for verification
- The employee’s movement is tracked through subsequent access points
- All events are logged with timestamps and correlated video evidence
This integration creates multiple security layers that are difficult to circumvent while generating actionable intelligence about facility usage patterns.
Beyond Basic Integration: Creating a Security Ecosystem
Advanced integrations between access control and other systems deliver powerful operational benefits:
- Video + Access Control: Visual verification of access events, video evidence of tailgating attempts, and automatic camera positioning based on access alerts
- Intrusion + Access Control: Automatic arming/disarming based on access credentials, differentiated responses for authorized vs. unauthorized entry during off-hours
- Environmental Sensors + Access Control: Occupancy monitoring, automatic lockdowns during environmental threats, and emergency response coordination
- Visitor Management + Access Control: Streamlined guest check-in, temporary credential issuance, and visitor movement tracking
Organizations increasingly seek these unified approaches to maximize both security effectiveness and return on security investments. Access control solutions are essential tools for enhancing security in organizations of all sizes, providing tailored systems that integrate advanced technologies and software to ensure secure environments for employees and visitors.
Cloud vs. On-Premise Access Control Systems
One of the most significant decisions when implementing access control is choosing between cloud-based and on-premise architectures. Each approach offers distinct advantages and considerations that impact security, operations, and total cost of ownership.
Cloud-Based Access Control Architecture
Cloud-based systems represent the modern approach to access control deployment:
- System Architecture: Core hardware like readers and controllers remain on-site, while management software, databases, and processing occur in the cloud
- Deployment Advantages: Faster implementation with minimal on-site infrastructure, simplified remote management, and automatic updates without IT intervention
- Operational Benefits: Centralized management across distributed locations, real-time system visibility from anywhere, and reduced maintenance burdens
- Investment Model: Lower initial capital expense with predictable subscription-based operational costs
- Scalability: Easily scales from small deployments to enterprise-wide implementations without significant infrastructure changes
- Resilience: Built-in redundancy, automatic failover, and disaster recovery provided by cloud infrastructure
The cloud architecture particularly benefits organizations with multiple locations, limited IT resources, or requirements for remote management capabilities. Access management systems play a crucial role in implementing robust access control policies and ensuring authorized use of resources, thereby minimizing security risks associated with unauthorized access.
On-Premise Access Control Architecture
Traditional on-premise systems continue to serve specific organization needs:
- System Architecture: All system components—hardware, software, servers, and databases—reside within the organization’s physical infrastructure
- Deployment Characteristics: More extensive on-site infrastructure, locally-managed servers, and organization-controlled update cycles
- Operational Considerations: Local network management, on-site administration, and internally-managed maintenance
- Investment Model: Higher initial capital expense with potentially lower long-term operational costs for specific deployment scenarios . At times, on-premise systems can result in high maintenance and unplanned costs due to reliability issues and multiple points of failures.
- Scalability: Expansion may require additional hardware investments and on-site configuration
- Resilience: Operates independently of internet availability but requires organization-managed system redundancy
On-premise architectures may better serve organizations with strict data sovereignty requirements, existing infrastructure investments, or specialized operational needs. System administrators play a crucial role in managing these systems, utilizing automated provisioning systems to configure user permissions according to established access control policies and job responsibilities.
The optimal choice depends on specific security objectives, IT resources, multi-site requirements, budget structures, and long-term scalability needs.
Choosing Cloud-Based Physical Access Control Systems: Key Considerations
For organizations leaning toward cloud-based solutions, several critical factors should inform selection:
- Scalability: The system should be able to grow with your organization, accommodating an increasing number of users and access points without significant overhauls.
- Integration: Ensure the system can seamlessly integrate with existing security infrastructure and other business systems, such as HR databases and visitor management systems.
- User Experience: The system should be user-friendly, providing a smooth experience for both administrators and end-users.
- Security: Robust security measures must be in place to protect sensitive data and prevent unauthorized access.
- Cost: Evaluate the total cost of ownership, including initial setup, ongoing maintenance, and potential upgrades.
Additionally, mobile access control is an innovative solution that empowers users to gain access to secured spaces using smartphones, offering enhanced security, cost reduction, and convenience.
Security and Data Protection
Evaluate end-to-end encryption protocols, multi-factor authentication for administration, data sovereignty considerations, compliance certifications relevant to your industry, and clear data ownership policies. Additionally, consider the importance of access control credentials in enhancing security and managing entry to restricted areas.
System Reliability and Performance
Consider guaranteed uptime percentages, latency specifications for access decisions, offline functionality during internet disruptions, backup mechanisms, and performance during peak usage.
Access controls play a crucial role in verifying identities and authorizing access to sensitive resources, ensuring both security and compliance.
Integration Capabilities
Assess pre-built integrations with popular systems, APIs for custom integrations, mobile device compatibility, support for industry standards, and future compatibility with emerging technologies. Additionally, ensure that these integrations secure connections to computer networks, system files, and data to maintain robust security measures.
Total Cost Considerations
Look beyond the subscription price to understand initial hardware investments, installation costs, pricing structures, additional fees for advanced features, scalability costs, and contract requirements.
Finding the best access control solution is crucial to ensure cost-effectiveness and enhanced security across various facilities.
Rhombus for Simple and Secure Access Control
Rhombus provides a cloud-managed physical security platform that unifies access control with other critical security functions. This consolidated approach eliminates traditional siloed systems in favor of a seamless, integrated security experience. Access control readers play a crucial role in this solution, offering features like easy installation, multi-technology support, and added functionalities such as built-in video and intercom capabilities.

The Rhombus access control solution offers:
- Enterprise-grade security with simplified deployment and management
- Native integration with video surveillance, sensors, and alarm monitoring for comprehensive situational awareness
- Flexible authentication including secure mobile credentials, key cards, and fobs.
- Real-time detections with instant alerts for unauthorized access attempts
- Centralized cloud management for multi-location visibility
- Automatic updates that continuously enhance security and feature sets
By consolidating physical security systems into one platform, organizations eliminate silos, reduce management complexity, and gain unprecedented insights through correlated security data.
If you’re evaluating options to enhance your physical security posture, contact us for a free trial or expert consultation on implementing an effective access control strategy tailored to your business needs.
Rohan Hemrajani serves as Director of Product & Content Marketing at Rhombus. He has over 10 years of marketing experience, ranging from multinational to startup brands, with the majority in the IoT industry. Rohan has launched several new products and programs designed to deliver safety and efficiency across diverse industries.