Security Convergence: Why Physical Security requires a Cybersecurity focus

This article was originally published in the January 2025 edition of Internal Security Journal. To access this edition, click here.
Protecting assets is perpetually a top issue for physical security professionals. But whether addressing the safety of items and spaces (theft, vandalism and break-ins) or the safety of people (staff and customers), physical security isn’t a one-size-fits-all proposition. Physical security standards are evolving as technology advances and industry expectations shift.
Today’s best physical security practices are focused on future-proofing their initiatives with technology that will evolve with an organization’s needs for years to come. Open platforms and cloud-based physical security solutions, which are easier to integrate across installations than traditional on-premises systems, deliver the advanced functionality that professionals now demand.
With the rise of cloud-based physical security comes the need to prioritize cybersecurity - not as a separate or siloed area, but integrated into physical security solutions. More than three-quarters (77%) of the physical security professionals surveyed “consider cybersecurity to be a high or very high priority” as reported in our most recent State of Modern Physical Security Report. This physical and cyber convergence requires a fresh look at approaches and best practices.
Data security: Essential for Physical Security Innovation
Video surveillance and access control remain foundational to physical security. Innovation in this space is moving well beyond the traditional - and inefficient - on-prem systems, though. These systems often create unexpected vulnerabilities when organizations attempt to modernize them.
To enable remote access capabilities, legacy systems commonly rely on port forwarding - a technique that exposes internal services to the internet by opening specific ports in the firewall. This makeshift solution creates additional attack vectors for malicious actors, as each forwarded port becomes a potential entry point for cyber-threats. Without proper security controls, these exposed access points can compromise the entire security infrastructure.
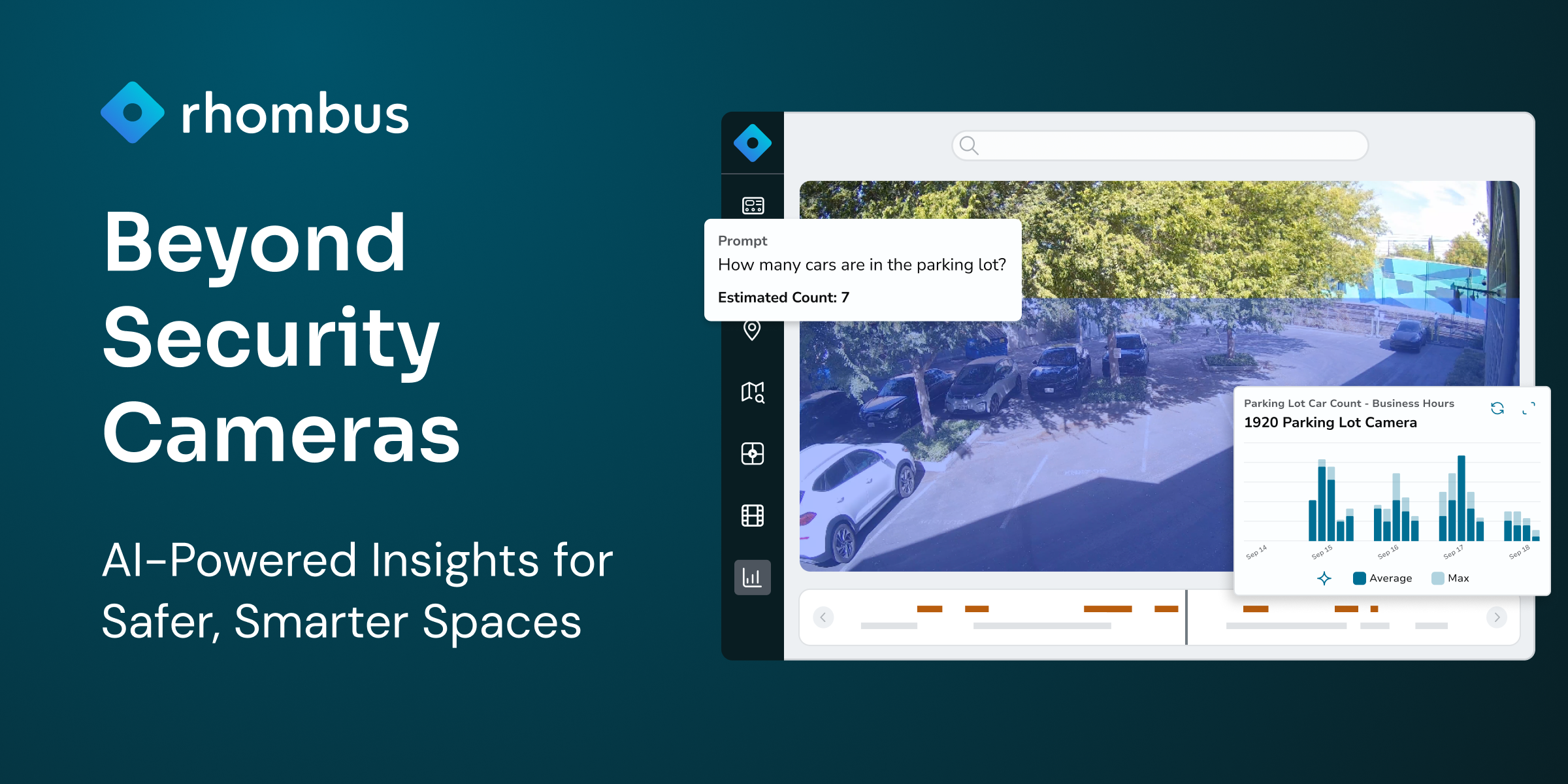
Cloud-based solutions can provide secure, native remote access for cameras, loT sensors, such as those for environmental monitoring, motion detection and entry monitoring, and access control (including door controllers, door readers, intercoms and secure cards). Supporting these solutions with an open cloud platform and video analytics makes management significantly easier to use at scale, whether at a single location or across 100s, with l0s or 1,000s of cameras.
When a physical security incident occurs and needs investigation, relevant footage can be identified in minutes, not hours, because of comprehensive visibility across locations and the ease of multi-camera investigations. And when suspicious activity is detected—based on AI analytics of 24/7 monitoring—real-time alerts with synchronized footage speed incident response times to potential physical security threats.
However, cloud platforms also come with their own cybersecurity risks. With the use of cloud-based solutions comes the imperative to integrate cybersecurity into physical security operations. Data and personally identifiable information (PII) must be properly secured against cyberattacks and malicious activity. When cybersecurity isn’t prioritized, the ramifications can be significant. For example, when video footage (such as that of patients in hospitals and clinics) isn’t secured, it can potentially contribute to Federal Trade Commission sanctions.
Combatting Risks
Combatting the cybersecurity and data security ramifications of cloud-based physical security initiatives require adherence to best practices. These include:
- Encryption: All media must have end-to-end encryption.
- Authentication: Comprehensive authentication includes mutual authentication, two-factor authentication (2FA), and protection against man-in-the-middle attacks.
- Audits: Regular third-party audits help ensure the quality and results of cybersecurity initiatives.
- Automation: Automation of verified firmware updates and health monitoring are among the areas of efficiency that are necessary for effective cybersecurity initiatives.
- Access controls: Strict data privacy protocols must be implemented. For example, rather than a “super admin” mode, system access must be grated explicitly.
Additionally, comprehensive compliance initiatives must be in place to ensure that all parts of the security initiative meet relevant guidelines, without creating an opening for regulatory sanctions. Initiatives must meet the guidelines for:
- Governmental regulations, such as the U.S. National Defense Authorization Act (NDAA) which defines that all hardware must be procured from white-listed manufacturers for cybersecurity purposes, and the General Data Protection Regulation (GDPR), governing information privacy in the European Union.
- Data privacy and security, such as System and Organization Controls 2 (SOC 2), which governs security compliance and data security standards, and
- Industry-specific compliance requirements, such as the Health Insurance Portability and Accountability Act (HIPAA), with guidelines for the protection of the personal health information (PHI) of medical patients; the Payment Card Industry (PCI) compliance, to protect cardholder data and sensitive authentication data; and the Criminal Justice Information Services (CJIS) requirements of criminal justice and law enforcement-related data.
How Rhombus integrates Cybersecurity into Physical Security Solutions
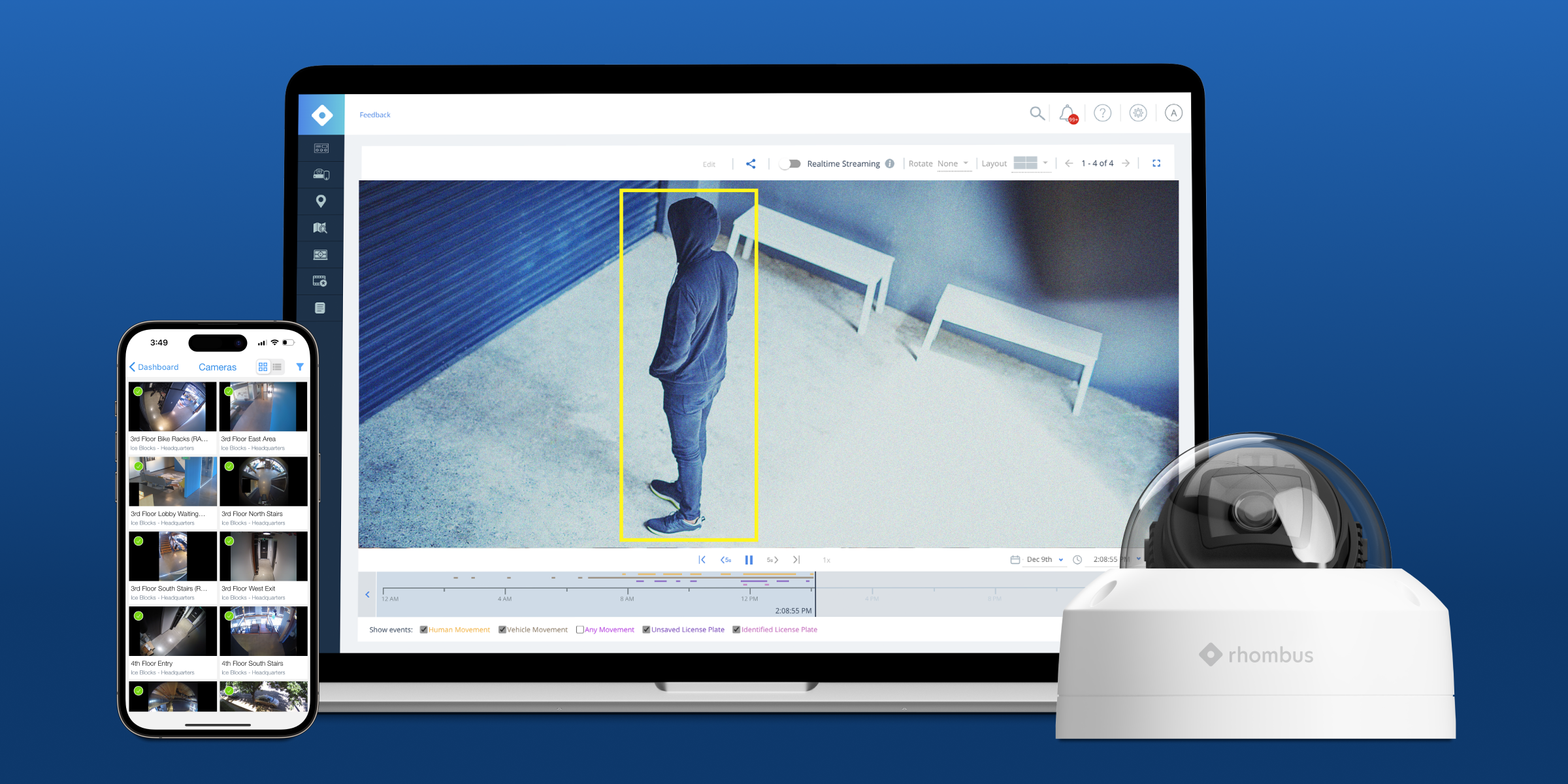
Cybersecurity is at the heart of how Rhombus approaches physical security solutions. With backgrounds in security intelligence, security architecture, engineering, and product management, our founders have always understood and prioritized the role that cybersecurity plays for a cloud-based physical security platform. That’s why Rhombus is built with a secure-by-default architecture.
Rhombus prioritizes the cybersecurity of physical security data. This means focusing on security, data privacy, and compliance for a trustworthy security platform.
Adherence to strict cybersecurity and data privacy regulations ensure that physical security systems are protected to the fullest extent of modern technology and industry best practices. Rhombus also maintains compliance with the varied regulations that impact the industries we serve, including education, food & beverage, government, healthcare, manufacturing, retail, and storage & warehouse.
The built-in data privacy protections of our platform include:
- Strict access protocols, meaning that no one except authorized end users at an organization have the authority to initiate and provide account access to support or partners.
- Granular permissions, with role-based access so that users have exactly as much access to physical security information as administrators want—no more and no less.
- Secure sharing, allowing users to quickly and securely share livestreams and video clips without extending system access. Passwords and expiration dates are used to maintain tight control over and safe communication of footage.
- Secure log-ins, protected by single sign-on and multi-factor authentication. Rhombus infrastructure doesn’t rely just on username and password; it is integrated with a customer’s preferred SSO provider and requires 2FA tokens that change every 30 seconds.
- Audit system access, with comprehensive access records. All granted access is logged and can be revoked anytime.
Rhombus is also a whitelisted manufacturer of hardware that is NDAA- and Trade Agreements Act (TAA)-compliant. All Rhombus hardware (including cameras, IoT sensors, and access control devices) is designed in-house and backed by a 10-year warranty. Continuous Benefits of a Converged Approach
Continuous Benefits of a Converged Approach
This converged approach to building trustworthy cloud-based physical security system pays off. Rhombus customers report robust physical security initiatives, with significant efficiencies and cost savings.

By preventing theft in high-risk areas and reducing their bottom line, an innovator in smart locker technology reported saving $250,000. A housing authority drastically reduced the time required to investigate video footage, using Rhombus to find an incident in 10 minutes, rather than the 20 hours it had previously taken. A YMCA system with 13 full-service facilities and more than 100 school-based sites was able to scale and unify its approach to physical security, replacing an outdated patchwork approach that didn’t meet insurance requirements for high-risk areas, like swimming pools. Bringing physical security initiatives up to date and to scale is now possible with cloud-based systems, it simply isn’t sustainable without being paired with a focus on cybersecurity.
Brandon Salzberg is a VP of Engineering at Rhombus and was the founding member of the Software Engineering team. With 20 years of experience in engineering and deep expertise in the security industry, Brandon has played an instrumental role in the creation of Rhombus’ secure, open, and flexible platform infrastructure.